Resources & Information
A knowledge resource for Executive Outliers guiding Their organizations through change, accelerating their vision, and building equity growth.
Book a Discovery Call
Read this post →
Compete by stepping outside the box November & December of last year, we started…, “Stepping Outside the Box” with our online solutions that build Exponential Equity Growth, while maintaining linear cost growth. The last few months we’ve started reorganizing with the announcement of our new year’s resolutions. Our New Year’s Resolutions In support of resolution […]

Read this post →
One of the biggest blockers to business growth is the IT Department or IT Support vendor. At first, this seems counter-intuitive. Technology is mission-critical when it comes to modern businesses. How could the IT department be a blocker? Well, every 18 months, there are significant changes and innovations in every technology for every industry. Each […]

Read this post →
In this 1 Hour and Q&A lecture at the Miami Herbert business school, Steve Kaplan of Jefferies Financial Group, “What Do We Know About Private Equity Performance?” Guest Lecture by Steve Kaplan at Miami Herbert, Private Equity has switched its investment priority. Instead of expense reduction, to Operations Optimization. This matches our objectives at Executive […]
Read this post →
by James Murray, on May 3, 202022 6:13:00 PM When I began networking I was very comfortable with servers and in server rooms. On the other hand, I have a very low social IQ and had no business networking strategy. Comfortable in a server room does not prepare you for a room of networkers. While some […]

Read this post →
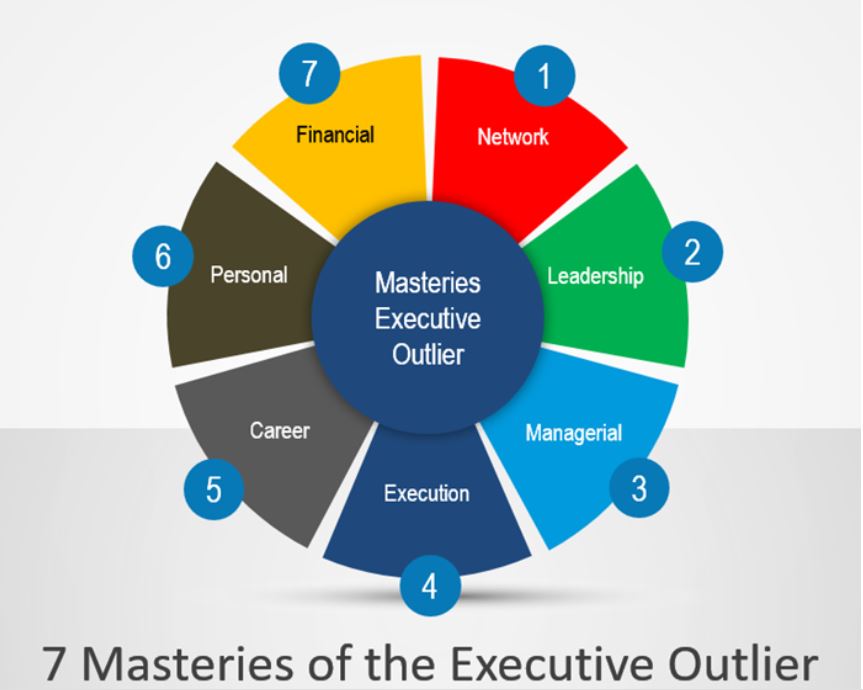
by James Murray, on Nov 7, 2022 What makes an Executive Outlier? If we map all executives on a bell curve, we can compare executives by industry norms. However, there are exceptions. How do we compare executives like Andrew Carnegie, Jack Welch, or Elon Musk, who fall well outside the standard executive bell curve? These leaders […]